OWASP ZAP Engine
Deep integration with OWASP ZAP to detect SQLi, XSS, and misconfigurations with industry-standard precision.
The Exploit Finder platform allows companies and experts to perform complete OWASP Vulnerability Checks with continuous analysis and professional reports.
Based on certified engines, our Vulnerability Scanner detects criticalities and guides remediation with strategic documents for the board and technical teams.
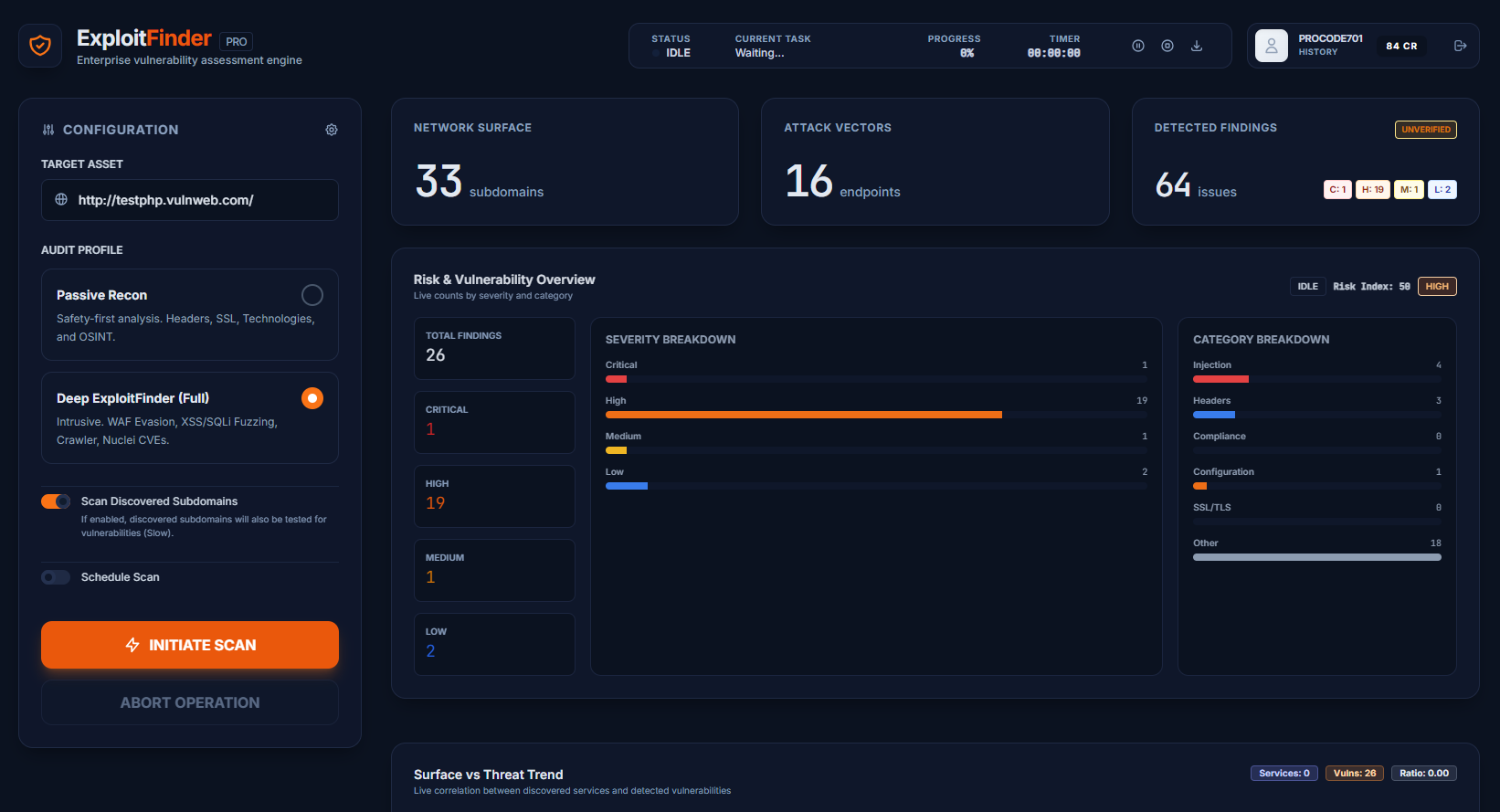
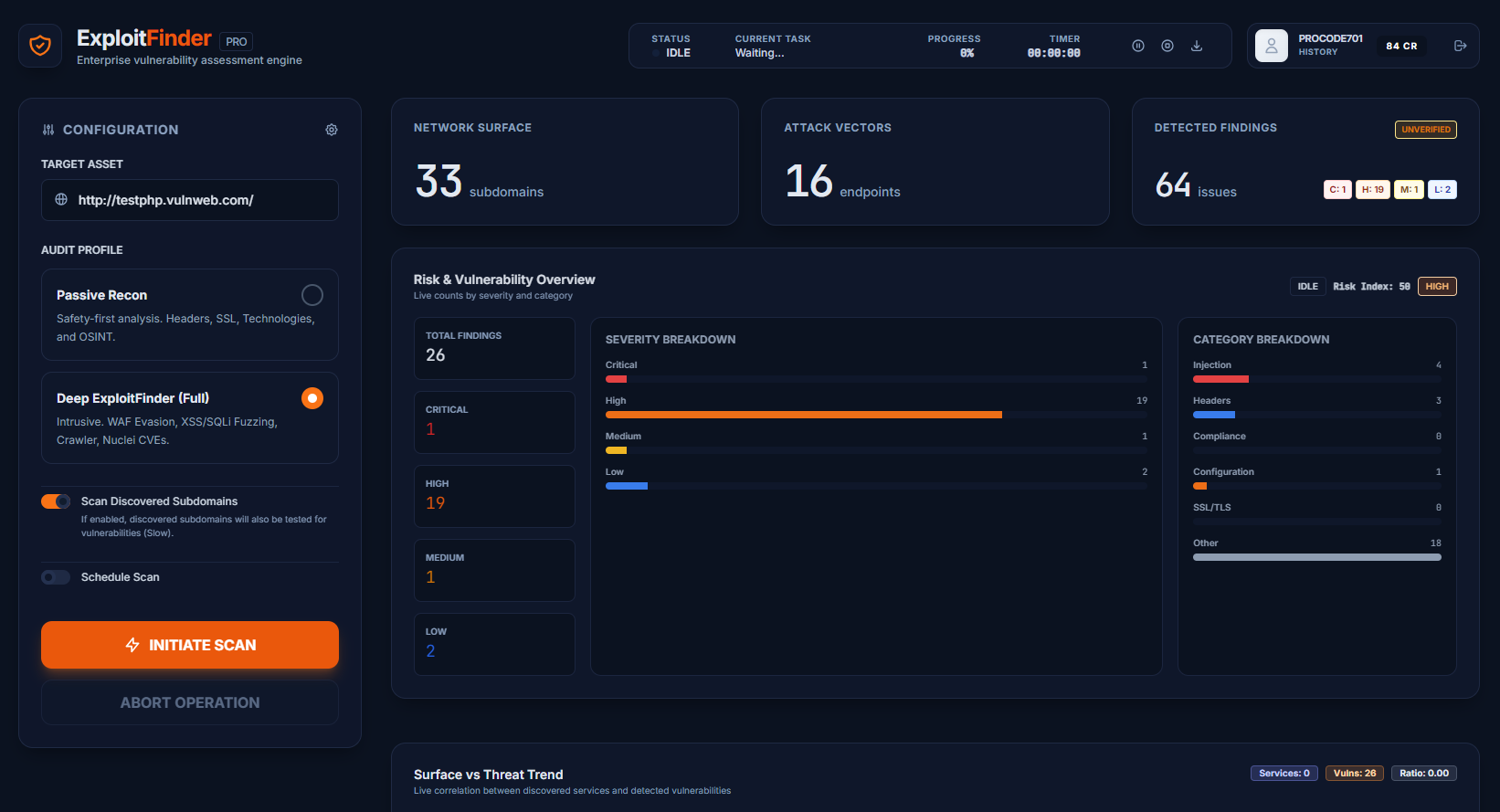
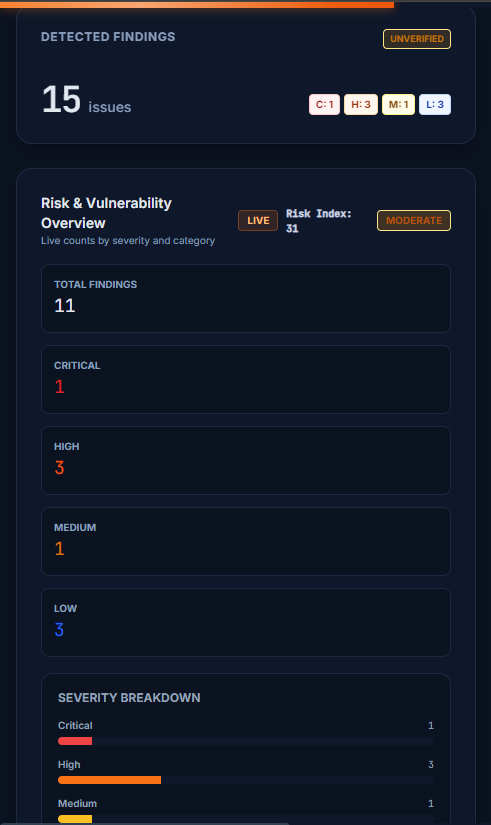
Real vulnerability analysis documents. Not simple automatic logs, but operational and continuous intelligence.
Business language for the board, understandable without technical jargon.
Technical details, Proof of Concept, and reproduction steps for developers.
Not just "what's wrong," but "how to fix it" with time priority.
Automatic mapping to ISO/IEC 27001 and GDPR standards.
The core of our scanner includes the best OWASP ZAP signatures, enhanced by business logic analysis. We offer a complete, validated, and historicized Online Vulnerability Scan.
Deep integration with OWASP ZAP to detect SQLi, XSS, and misconfigurations with industry-standard precision.
Subdomain enumeration, directory mapping, and exposed JavaScript asset analysis.
Service enumeration and component fingerprinting with vulnerability correlation.
Verification workflow to reduce false positives and qualify real impact.
Detection of new CVEs and risk variation continuously between reports.
Ranking findings by technical risk, exploitability, and business impact.
Readable document for stakeholders and technical detail for the operational team.
Remediation guidance ready for structured patching and hardening workflows.
Risk synthesis, priority, and remediation roadmap with supporting evidence.
Each report cycle follows a stable 6-phase pipeline, designed to reduce noise, increase confidence, and accelerate remediation decisions.
We map domains, endpoints, and application surfaces to define the real perimeter.
We classify stacks and components to find exposures and relevant vulnerabilities.
We cover classic applications and SPAs with a state-aware approach for hidden endpoints.
We stress application controls with dynamic testing and targeted detection.
We responsibly simulate critical vectors to validate real technical impact.
We convert technical data into operational priorities and roadmaps with clear ownership.
Engines used and orchestrated internally: Subfinder, FFUF, ZAP, Nuclei, XSStrike, SQLMap, Commix, and proprietary correlation scanners.
The market is full of one-shot scans that deliver noisy output. We adopt a different strategic model: recurring reports, delta comparison, and operational priorities.
Difference 1
We don't stop at detection: every report includes priorities and an actionable plan.
Difference 2
We measure how posture evolves, not just the state of a single day.
Difference 3
Single document for stakeholders and operational team: less friction, more execution.
Where traditional solutions provide static snapshots, Exploit Finder ensures resilience and proactive governance.
Traditional Approach
Static output limited to execution time. No risk historicization or strategic decision support for remediation.
Exploit Finder Pro
Continuous governance with 12 annual audit cycles. Delta analysis and guided prioritization technology for remediation workflows.
Exploit Finder Enterprise
Continuous high-frequency surveillance for critical environments. Rapid detection of configuration drifts and emerging Zero-Days.
Assessment methodology aligned with recognized frameworks: reconnaissance, fingerprinting, misconfiguration review, vulnerability validation, and remediation guidance.
Across the world, we all have different ways to demonstrate our cyber security strategy. For many businesses using a good governance framework is a great way to demonstrate to clients, regulators and investors how seriously you take IT Governance.
Exploit Finder has a compliance engine built into the platform allowing you to export evidence data for a wide range of IT Governance Frameworks including but not limited to:

Choose continuity. Give real value to security with our managed OWASP scan plans.
Technical Assessment
Verify our engine quality.
Certification Audit
Ideal for punctual pre-release validation or spot compliance.
Cyber Governance Plan
The strategic choice to maintain security posture over time.
With Exploit Finder, receive concrete, understandable periodic reports oriented towards technical action. Zero noise, maximum operational utility.
Talk to an Advisor